Spectacular price movements of digital cryptocurrencies and the search for more and more areas of application for blockchain technologies have brought the topic area increasing public attention in recent years. But what is blockchain anyway, and what is the relationship between cryptocurrencies and data protection and open source? Contrary to the existing sensational reporting, we would like to factually and informatively review this current topic with this blog article.
What is a Blockchain?
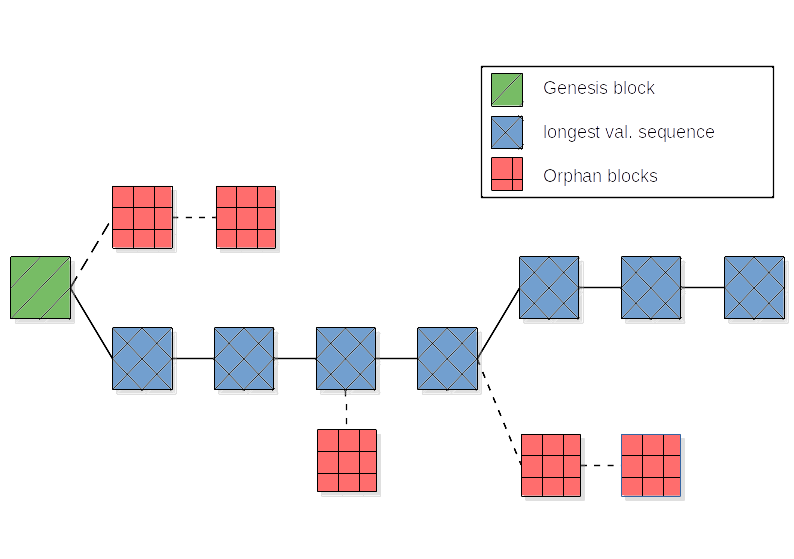
The white paper on Bitcoin from 2008 was the first to systematically describe the concept of a blockchain and its application. Thus, it is a relatively young technology. Defining and explaining the term ‘blockchain’ is relatively complex. Therefore, links are added to important technical terms that contain further explanations and at the end of the section, the introductory graphic is discussed. [1]
A blockchain is a real-time list that stores records in the form of encrypted blocks (“block”). The individual blocks can be copied identically and decentrally to individual devices and chained (“chain”) or synchronized with each other (peer-to-peer network). If changes are made to the data sets, this leads to a change in all blocks. Each block typically has its own cryptographically encrypted hash (scatter value) of the previous block, a timestamp and transaction data. Such a hash function is used to check the integrity of the data sets, i.e. a hash ensures the correctness of the data in the blocks as well as their unique allocation. While the timestamp is necessary to assign events, such as a transaction with a cryptocurrency, to an exact point in time, the transaction data is used to convey the content information of a transaction, such as the amount. [2, 3, 4]
The blocks are arranged in specific sequences or an order and can thus be transparently tracked and validated all the way to the beginning of the chain using consensus methods. The most common consensus methods are proof-of-work and proof-of-stake methods.
In the case of proof-of-work, complex mathematical tasks are usually assigned, where a participating person receives a reward, e.g. in the form of Bitcoins, for solving the mathematical problem to create an incentive to participate. In the process, a new block is generated with a hash, the correctness of which is itself verified by other nodes across the network. If the solution is correct, this calculated block is added to the blockchain. The degree of difficulty of the mathematical task often depends on the number of participants. If more people work on generating new blocks, i.e. if more computing power is used overall, the complexity of the task increases in order to artificially limit the number of blocks and at the same time make the complete system more secure. Attacks (‘51% attack‘) as well as faulty transactions thereby also require more computing power and make them unlikely and unprofitable.
In contrast, proof-of-stake is not based on a competitive race for computing power, but on a weighted random mechanism, whereby a participating person is “randomly” determined who is authorized to validate the network and generate a new block of the chain. The weighting means that the more so-called tokens, for example units of cryptocurrency, a person holds, the more likely that person is to be selected by the mechanism.
The described methods create unity (‘consensus’) within the decentralized network, thus circumventing, among other things, the so-called ‘Byzantine Fault’. [2, 5]
For completeness of the description of blockchains, it should be said that blockchains are a so-called distributed ledger technology (DLT). The term originates from accounting and means that the ledger is not maintained by a central entity, but decentralized copies are distributed across multiple parties and changes in individual copies are automatically reflected in all other copies. Unlike the blockchain, however, a DLT does not necessarily have to involve a specific sequence of blocks or a consensus mechanism. [6]
Thus, referring back to the diagram at the beginning of this section, the green block represents the beginning of the chain (genesis block). While the blue blocks represent the longest validated sequence and thus the main chain, the red blocks represent so-called ‘orphans’, blocks that could not be further validated. Thus, the graphic represents the sketch of a blockchain.
Practical Applications
The best-known application example of blockchain technology is, of course, cryptocurrencies such as Bitcoin or Ether. Proponents of these cryptocurrencies see the technological advantage in the fact that, due to the blockchain, no third party (e.g. a bank) is needed to conduct secure and transparent transactions. Consequently, transaction costs decrease as well as the dependency on financial companies or government authorities.
In addition, blockchains are increasingly being used in so-called smart contracts. These are computer protocols that digitally map contractual agreements and often also verify their compliance, i.e., smart contracts can be described as automating the processes of contractual agreements. Specifically, such smart contracts and blockchains in general are already being used in other areas of the financial industry, away from cryptocurrencies, as well as in logistics to verify supply chains. [7]
In theory, numerous other application areas based on decentralization and automation come into consideration. So far, the technology has not been able to establish itself in many areas. In this context, it should be noted that critics of blockchain technology often acknowledge the technological achievements behind it, but fail to see concrete areas of application. One of the best-known critics is US computer security expert Bruce Schneier, who coined the following quote on the subject: [8]
Any company that relies on blockchain today could actually do without it. No one has ever had a problem that blockchain is a solution for. Instead, people are taking the technology and going after problems.
In other words, blockchain is a technological solution for which, however, no problem exists.
Blockchain & Data Protection

As the term ‘cryptocurrency’ already reveals, cryptography is a cornerstone of blockchains, i.e. any information within the blockchain is encrypted with algorithms. To stay with the Bitcoin example, this information includes, for example, the transaction amount, the transaction time, the sending and receiving persons or the hash. Encryption is used to ensure that this confidential information cannot be tapped and changed. Furthermore, without cryptographic methods, no new Bitcoins could be created either and thus the blockchain as a whole would not exist. At the same time, a blockchain also offers transparency, because the information can be viewed (in encrypted form) without it being possible to draw conclusions about specific individuals. Thus, blockchains are a technology that cover the important pillars of data security: transparency, traceability, immutability, decentralization and confidentiality. The recent update of the Bitcoin code, among others, has again increased data security. [9, 10, 11, 12]
At the same time, however, more critical voices exist regarding blockchain and data protection. It should be noted that both public and private blockchains exist. Public blockchains are public networks in which, in principle, everyone can participate, while access to private blockchains can be restricted by the owners or administrators. The latter, in a real sense, contradicts the basic idea of a blockchain, but is an existing practice and is discussed in more detail in the following section. [13]
When using modern, secure encryption algorithms, there is actually little attack area against data security within a public blockchain. Consensus mechanisms further enhance security, as an attempted manipulation would require the manipulating individual to control the majority of the network. Nevertheless, data protectionists point out that identification of private individuals could be possible at least at the moment when the blockchain information is realized, for example, when the bitcoin amount is exchanged for a real currency. Although the security of such networks is relatively high, data protectionists advise against storing confidential information on public blockchains. [9, 13]
Private blockchains theoretically have more privacy issues in comparison, as there are several ways to identify sensitive, personal data. On the one hand, this includes the user ID itself in order to participate in such a private network, which can remove the aspect of anonymity. In addition, there is a superordinate authority (owner or network administrator), which means that decentralization is equally non-existent. This higher-level person often has access to sensitive data that may be stored centrally and can make changes to the network himself. Security thus depends heavily on the trustworthiness of this person. Thus, not only decentralization and confidentiality are vulnerable, but also traceability as well as immutability. [9, 13]
Blockchain & Open Source

At least in the context of public blockchains, the term open source is often used. First of all, therefore, it should be clarified what ‘open source’ actually means. The term is usually used synonymously with the term ‘free software’, although it is disputed whether open source refers only to the public visibility of the code or also to free use. We would like to equate both terms for the sake of simplicity. Basically, open source software is defined by the following four freedoms: The freedom to openly view a source code, to use it, to modify it, and also to distribute it yourself. A detailed description can be found in our first blog post.
Just as a blockchain does not necessarily have to be public, it does not have to comply with open source principles. However, the basic idea of a blockchain code running decentrally on many nodes in a large network that does not belong to any higher authority – also implies a certain proximity to open source. So it is no coincidence that the best-known application, Bitcoin, is completely open source (under the MIT license). Thus, everyone has access to the entire source code, can use it and change it for their own purposes, although the existing blockchain network on which the well-known Bitcoin itself runs remains unchanged by this, since changing the code within the network requires its consensus. [14]
Open source lives in large part from an active community that discovers potential problems or security vulnerabilities in public source code and, if necessary, fixes them on its own. As was made clear earlier, this idea also applies in the case of open source blockchains, although these updates can only be implemented in the main network if the majority of the users agree via the consensus process. On the one hand, this promotes consistency and the certainty that no updates with clearly negative consequences for the users will find their way into the overall network, but on the other hand, it makes the system inflexible for meaningful improvements in the short and medium term. Due to this, the recently implemented Bitcoing update (‘Taproot’) is the first update in about 4 years [12, 14].
Critical Review

In addition to the accusation of a lack of useful applications, the lack of efficiency of long data chains and peer-to-peer networks in particular has been criticized. Blockchains require a large network of data centers and end devices, which keeps the system running: Large networks require large amounts of energy. In addition, elaborate consensus methods are used for coordination within the network. The proof-of-work method in particular is very energy-intensive in this context, since computing power is expended by a large number of nodes in the network to solve complex tasks and verify them. Thus, a high energy consumption is inherent to this method.
If we take Bitcoin as an example, it becomes clear that, according to estimates, only 30 countries worldwide consume more electricity in total than is required by Bitcoin. These estimates are around 80 to 120 terrawatt hours of electricity per year, which is higher than Belgium’s electricity consumption. In addition, over 60 percent of Bitcoin miners are located in China, where the amount of polluting coal-fired electricity is very high. [15]
Regarding data protection, some aspects have already been discussed in detail. In conclusion, it can be stated that, as with every application in the digital space, there are definitely concerns that should also be taken seriously in individual cases. However, blockchain technology in general does not show any fundamentally increased vulnerability of data security compared to centralized databases and other comparative systems, but is rather dependent on the concrete design of the encryption algorithms, consensus mechanisms and privacy protection.
Further criticism exists with regard to decentralization and anonymity. While supporters see this as an opportunity for greater freedom and privacy, critics warn that this anonymity could support crime. Particularly with regard to cryptocurrencies, the potential for illegal activity in the form of criminal trading and money laundering is a matter of public debate. Moreover, a large-scale establishment of decentralized cryptocurrencies would deny state institutions some options for economic policy control, especially monetary policy. However, it should be noted here that this might be an advantage rather than a disadvantage of cryptocurrencies from the opposing perspective. [16]
Finally, it should be noted again that the intention of this blog article is not to take a positive or negative stance on blockchain technology, but to explain this much-discussed topic in a factual manner. The topic of blockchain is certainly interesting and technologically impressive, but whether it will have a major impact on society in the long term remains to be seen.
Sources
- Nakamoto, Satoshi (2008): Bitcoin – A Peer-to-Peer Electronic Cash System. Online at: bitcoin.org.
- Schlatt, Vincent; Schweizer, André; Urbach, Nils und Fridgen, Gilbert (2016): Blockchain – Grundlagen, Anwendungen und Potenziale. In: Fraunhofer-Institut für Angewandte Informationstechnik. Online at: frauenhofer.de.
- The Economist (2015): The great chain of being sure about things. Online at: economist.com.
- SAP (2021): Was ist die Blockchain-Technologie? Online at: sap.com.
- Joos, Thomas und Schmitz, Peter (2021): Konsens-Algorithmen in Blockchains. Online at: blockchain-insider.de.
- Benjamin, Godfrey (2021): Blockchain vs. Distributed Ledger Technologie (DLT) – Was ist der Unterschied? Online at: imiblockchain.com.
- Prinz, Wolfgang und Schulte, Axel (2017): Blockchain und Smart Contracts – Technologien, Forschungsfragen, Anwendungen. In: Fraunhofer-Institut für Angewandte Informationstechnik. Online at: frauenhofer.de.
- Schneider, Oliver (2019): Warum das IoT tötet und wir für Google zahlen sollten. Online at: netzwoche.ch.
- Rosenthal, Simone und Schmitz, Peter (2020): Ist Blockchain und Datenschutz zusammen möglich? Online at: blockchain-insider.de.
- DSGVO Support (2021): Blockchain und Datenschutz. Online at: dsgvo-support.de.
- Schiller, Kai (2018): Die Rolle der Kryptographie innerhalb der Blockchain-Technologie. Online at: blockchainwelt.de.
- Sigalos, MacKenzie (2021): Bitcoin just got its first makeover in four years. Online at: cnbc.com.
- Salzgeber, Ramona (2019): Öffentliche und private Blockchains – Worin bestehen die Unterschiede? Online at: ico.li.
- BitcoinCore (2021): Quellcode Bitcoin. Online at: github.com und bitcoincore.org.
- Rooks, Timothy (2021): Der unersättliche Stromfresser – Bitcoin. Online at: dw.com.
- Zengerling, Zita und Robben, Timo (2021): Kriminellen auf der Spur. Online at: tagesschau.de.
Pascal founded ViOffice together with Jan in the fall of 2020. He mainly takes care of marketing, finance and sales. After his degrees in political science, economics and applied statistics, he continues to work in scientific research. With ViOffice, he wants to provide access to secure software from Europe for everyone and especially support non-profit associations in their digitalization.